RabaCTF 2025 Capture The Flag
RabaCTF is an Attack-Defense CTF from the ECSC Estonian team.
RabaCTF 2025 hosted 19 teams from around the world with over 100 attendees.
RabaCTF is on hiatus until 2026 :) See you later!
RabaCTF is an Attack-Defense CTF from the ECSC Estonian team.
RabaCTF 2025 hosted 19 teams from around the world with over 100 attendees.
RabaCTF is on hiatus until 2026 :) See you later!
Attack-Defense CTFs are fun with a team. Play RabaCTF with a 5-10 person team. Assign 1-2 players the role of Administrator, and divide up the web services among the others.
Meeting up with your team is highly recommended - however the CTF will be run remotely and each player will be given a WireGuard client config to access the game.

Your team is in charge of maintaining a Vulnbox with 4 custom made web services. Protect, monitor, and keep the Vulnbox running whichever way you can.
The organizers of RabaCTF will prepare the Vulnbox for your team and send connection instructions before the CTF.
A 1-hour familiarization period will be allotted at the start of the CTF, before the network opens and connections between teams are possible.
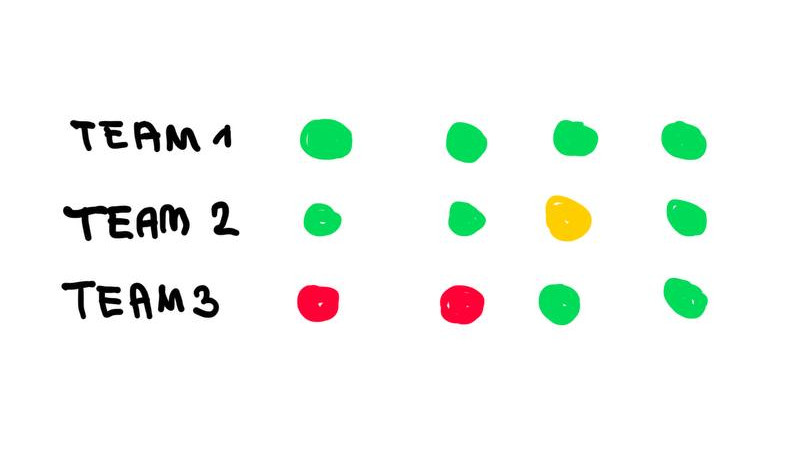
Every tick (2 minutes), the Checkerbot will visit your Vulnbox and simulate a user. The Checkerbot registers, logs in, and interacts with all of the web services. It will also save a Flag somewhere in each web app.
Make sure the web app is working and Flags are not deleted! The Checkerbot will look at the 5 last historical ticks to find flags it has planted.
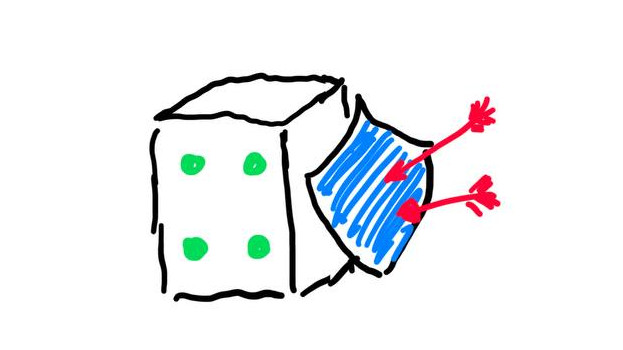
Every web service has vulnerabilities, logic bugs, authorization errors etc. Find the vulnerabilities and patch them. This way you protect the Checkerbot's data.
Points are subtracted every time a Flag given to you has been sent to the Gameserver. Don't bleed points - patch!
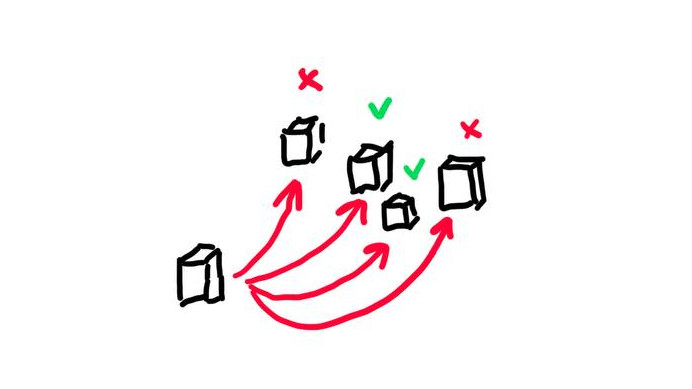
If you find a vulnerability, use it against the other teams! Any flags you are able to extract can be handed in to the Gameserver for points.
It can get tedious to attack every team every 2 minutes. You should script and automate the attacks!

Capture all packets going in and out of your Vulnbox. This way you can see if someone is attacking you. You may also gain hints about what your web services are doing!
Analyzing the packet log can also help you invent filtering rules. If you want a WAF, you have to install it!

Projekti viiakse ellu Eesti Interneti SA abiga.
We thank the Estonian Internet Foundation for their sponsorship of RabaCTF 2025. Thanks to their support, we were able to cover the costs of video production, cloud hosting and challenge development.
Stay posted by watching this website!